Disabling Proxy Connections In AnyConnect
- By Joe Astorino
- November 10, 2011
- 9 Comments
Introduction
I ran into an interesting problem at work yesterday, and wanted to share the solution. I did quite a bit of digging on it myself, and I learned a lot about how Cisco Anyconnect integrates with Microsoft Internet Explorer. There were a few posts out there on this, but none that really solidified things for me. I would like to thank Jody Lemoine (@ghostinthenet on twitter) for helping me solve this one! Also, the supporting documentation for much of this is here
So, the team here at work has recently been experimenting with a new proxy server service from Cisco Scansafe. As part of the experimentation phase, the windows guys have also been experimenting with integrating the proxy configuration into MS IE. What they did is enter the proxy PAC file path in the IE proxy server settings area (under the options/connections tab) and then through group policy actually disabled users from seeing that tab at all, thus preventing people from changing it. Great, so what does that have to do with AnyConnect
Well, I have an ASA firewall at home that runs SSL VPN. We also do business with other companies that our users sometimes need to SSL VPN into from inside our network using the Cisco AnyConnect client. This is where the problem started. I needed to access my home network for a second so I fired up AnyConnect as usual and started my session. I authenticated just fine as normal, and received my normal login banner. Then the problem occured — AnyConnect switched to a new screen I had never seen before asking for proxy credentials. The IP address of our proxy server was already filled in and it wanted a username, password and domain. WTF? I had not told AnyConnect to connect through a proxy. As I looked through the few options in the AnyConnect client itself, I realized there was no user selectable option to enable or disable a proxy server. How then could the client know about our proxy?
As it turns out, AnyConnect by default pulls down the proxy information set in Microsoft Internet Explorer and uses that proxy information to attempt to build the initial tunnel. Even if I could disable the proxy (which I couldn’t due to the connections tab being “gone”), that would be a pain in the butt and certainly not an option for regular users. What to do?
The Solution
When your AnyConnect client connects to the ASA and you authenticate, it pulls down an AnyConnect client profile. The profile is really just an XML file stored on the ASA that contains a whole slew of options for the client. There is a default profile, and you can also go ahead and create custom profiles, and tie those profiles to specific groups. This is how you solve the problem. There is an option you can add into the client profile to ignore MS IE proxy settings during initial tunnel setup. Cool!
Method 1
Usually, I am a CLI guy but for this, my preferred method was via the ASDM GUI. Why? The ASDM has a really nice AnyConnect profile creator/editor that allows you to simply check and uncheck options. When you do that, it is actually editing the XML file stored on the ASA. Much easier than downloading the XML file, editing it yourself, and uploading it back.
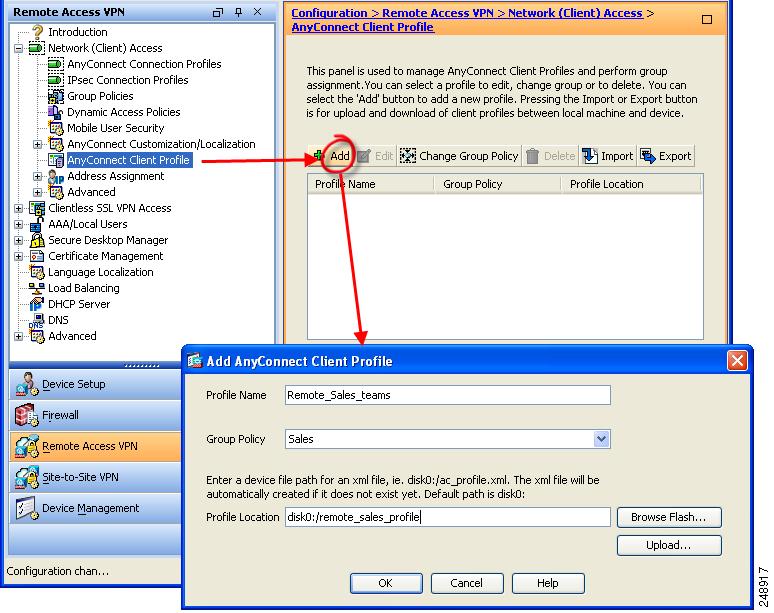
Go to configuration for Remote Access VPN. Then go to Network (Client) Access –> AnyConnect Client Profile. By default you won’t see any profiles. I created a specific profile so that I could edit it. Here is a screen shot
This will actually create the profile XML file on the ASA. Then all you have to do is go in and edit it. When you bring up the edit screen for your new profile, go ahead and click the Preferences (Cont) pane. In that section you will see a check box for “Ignore Proxy”. Go ahead and check it. Make sure your profile is associated with the proper Group policy and apply / save your configuration. You are done!
Here are the CLI commands for adding the profile and associating it to your group policy. Note that the CLI commands below just create the profile and tie it to the group policy, but they do NOT edit the XML file to disable the proxy. To do that you need to check the box I talked about above in the ASDM, or you need to manually edit the XML file yourself (Method 2).
webvpn svc profiles SSLClient disk0:/sslclient.xml ! group-policy SSLClient attributes webvpn svc profiles value SSLClient
Method 2
If you want to edit the XML file yourself instead of checking boxes in ASDM you can do it this way. Simply add the following to your profile XML file. You will need to download it from the ASA, edit it, then re-upload it to the ASA.
<ProxySettings>IgnoreProxy</ProxySettings>
Other IE Proxy Tweaks
What we just discussed was how to get the AnyConnect client to build the actual VPN tunnel without going through a proxy. In other words, bypass the proxy when building the initial tunnel. However, after the tunnel is built, there are other settings that come into play. Once you actually have a VPN connection, there are other settings in the group-policy that control what the IE proxy settings look like during the VPN session itself. All of these can be controlled with the msie-proxy command set from group-policy attributes mode
theboss(config)# group-policy SSLClient attributes
theboss(config-group-policy)# msie-proxy ?
group-policy mode commands/options:
except-list Set the IE Browser Proxy server exception list setting for
local bypass on the client PC
local-bypass Set the IE Browser Proxy local bypass setting for the client PC
lockdown Set the IE Browser Proxy lockdown setting for the client PC
method Set the IE Browser Proxy method setting for the client PC
pac-url Set the PAC URL
server Set the IE Browser Proxy server:port setting for the client PC
When I connect to a remote network using AnyConnect, I do not want the work proxy or any other proxy involved in any way so I configure msie-proxy method no-proxy under the group policy. Obviously there is more you can do there. For example, you can manually type in the proxy/port settings you want the client browser to use, you can add proxy exceptions, you can instruct their browser to bypass the proxy for local resources, you can even set the URL pointing to a PAC file if you want. Powerful stuff!

Fantastic! I was looking out for this. Fortunately I was evaluating both Cisco Scansafe & Anyconnect at the same time.
Nice doc….very userful…
nice one ! this saved me so much work , thankyou
[…] http://astorinonetworks.com/2011/11/10/disabling-proxy-connections-in-anyconnect/. […]
[…] http://astorinonetworks.com/2011/11/10/disabling-proxy-connections-in-anyconnect/ […]
Thanks!!
hi i am facing the same problem “the vpn connection is not allowed via a local proxy this can be changed through anyconnect profile settings”
But i am unable to resolve the error with methods you mentioned
help me out
Thanks In advance
Hi, thanks a lot for your post. Very helpful about
msie-proxy method no-proxy.
Hello
I have IgnoreProxy in .XML file but the errore message is the same